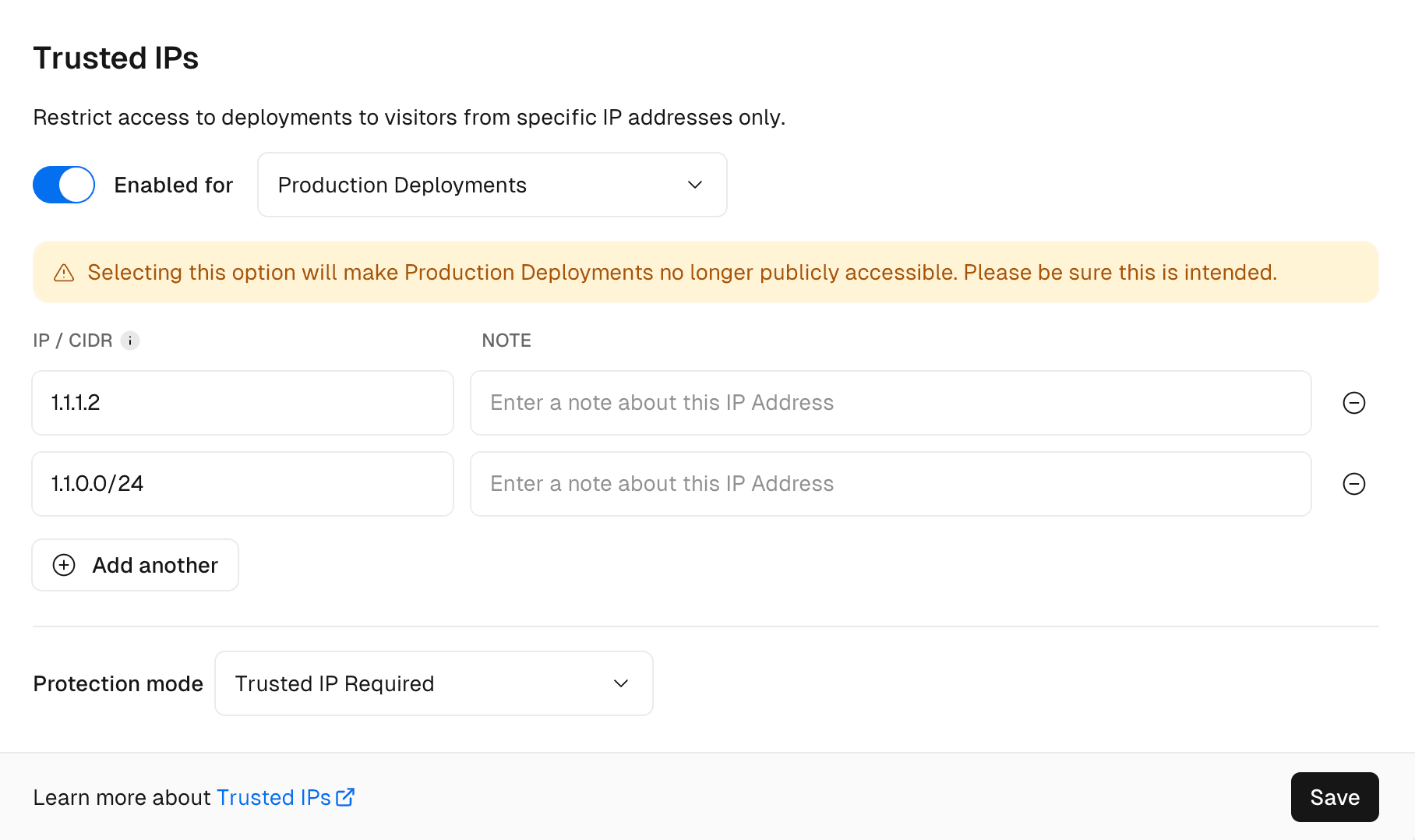
Trusted IPs
Trusted IPs are available on Enterprise plans
With Trusted IPs enabled at the level of your project, only visitors from an allowed IP address can access your deployment. The deployment URL will return 404 No Deployment Found for all other requests. Trusted IPs is configured by specifying a list of IPv4 addresses and IPv4 CIDR ranges.
Trusted IPs is suitable for customers who access Vercel deployments through a specific IP address. For example, limiting preview deployment access to your VPN. Trusted IPs can also be enabled in production, for example, to restrict incoming access to only requests through your external proxy.
The table below outlines key considerations and security implications when using Trusted IPs for your deployments on Vercel.
| Consideration | Description |
|---|---|
| General Considerations | |
| Environment Configuration | Can be enabled for different environments. See Understanding Deployment Protection by environment |
| Compatibility | Operates as a required layer on top of Vercel Authentication and Password Protection. |
| Bypass Methods | Can be bypassed using Shareable Links and Protection Bypass for Automation |
| IP Address Support | Supports IPv4 addresses and IPv4 CIDR ranges |
| Prerequisites | |
| Preview Environment Requirements | Can only be enabled in preview when Vercel Authentication is also enabled. |
| External Proxy Configuration | Requires rulesets configuration to avoid blocking proxy IPs. Contact our sales team for more information |
| Security Considerations | |
| Firewall Precedence | Vercel Firewall takes precedence over Trusted IPs |
| IP Blocking | IPs or CIDRs listed in IP Blocking will be blocked even if listed in Trusted IPs |
| DDoS Mitigation | Trusted IPs do not bypass DDoS Mitigation unless configured |
| Deployment Impact | Changing the Trusted IPs list affects all deployments |
| Disabling Trusted IPs | Disabling makes all existing deployments accessible from any IP |
You can manage Trusted IPs through the dashboard, API, or Terraform:
From your Vercel dashboard:
- Select the project that you wish to enable Trusted IPs for
- Go to Deployment Protection in the sidebar
Ensure Vercel Authentication is enabled. See Managing Vercel Authentication.
From the Trusted IPs section:
- Use the toggle to enable the feature
- Select the deployment environment you want to protect
- Enter your list of IPv4 addresses and IPv4 CIDR ranges with an optional note describing the address
- Finally, select Save
All your existing and future deployments will be protected with Trusted IPs for that project. Visitors to your project deployments from IP addresses not included in your list will see a No Deployment Found error page.
You can manage Trusted IPs using the Vercel API endpoint to update an existing project with the following body
deploymentTypeprod_deployment_urls_and_all_previews: Standard Protectionall: All Deploymentspreview: Only Preview Deploymentsproduction: Only Production Deployments
addresses: Array of addressesvalue: The IPv4, or IPv4 CIDR addressnote: Optional note about the addressprotectionModeadditional: IP is required along with other enabled protection methods (recommended setting)additional: IP is required along with other enabled protection methods
// enable / update trusted ips
{
"trustedIps": {
"deploymentType": "all" | "preview" | "production" | "prod_deployment_urls_and_all_previews",
"addresses": { "value": "<value>"; "note": "<note>" | undefined }[],
"protectionMode": "additional"
}
}
// disbale trusted ips
{
"trustedIps": null
}You can configure Trusted IPs using trusted_ips in the vercel_project data source in the Vercel Terraform Provider.
Was this helpful?

