Deployment Protection on Vercel
Deployment Protection lets you control who can access your preview and production URLs. You configure it at the project level, choosing both a protection method (how you protect) and a protection scope (what you protect).
On the Hobby plan, you can use Vercel Authentication with Standard Protection. This protects your preview deployments and deployment URLs, but your production domain remains publicly accessible. To protect production domains, you need a Pro or Enterprise plan. Deployment Protection requires authentication for all requests, including those to Routing Middleware.
You can choose from three methods to protect your deployments:
- Vercel Authentication: Restricts access to only Vercel users with suitable access rights. Available on all plans
- Password Protection: Restricts access to users with the correct password. Available on the Enterprise plan, or as a paid add-on for Pro plans
- Trusted IPs: Restricts access to users with the correct IP address. Available on the Enterprise plan
The protection scope determines which URLs you protect:
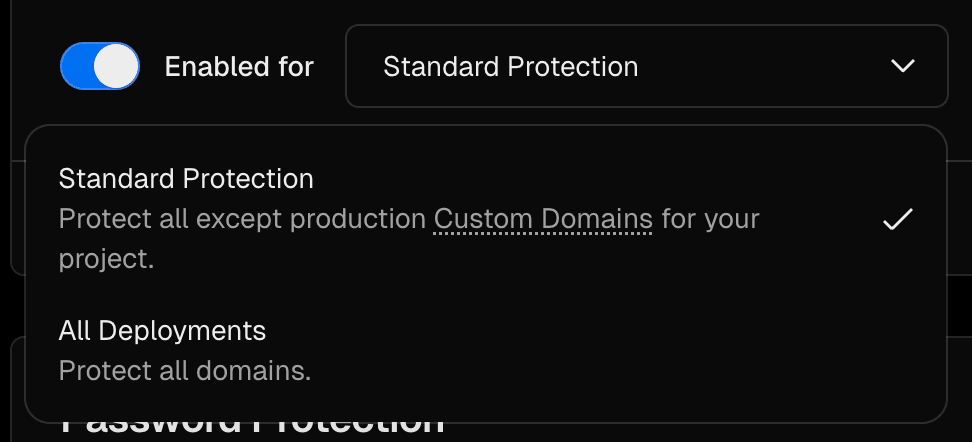
- Standard Protection: Protects all deployments except production domains. Available on all plans
- All Deployments: Protects all URLs, including production domains. Available on Pro and Enterprise plans
- (Legacy) Standard Protection: Protects all preview URLs and deployment URLs. All up-to-date production URLs remain unprotected.
- (Legacy) Only Preview Deployments: Protects only preview URLs. Does not protect past production deployments.
To protect only production URLs, use Trusted IPs. This option is only available on the Enterprise plan.
You manage Deployment Protection through your project settings:
- From the dashboard, select the project you want to configure
- Open Settings in the sidebar and select Deployment Protection
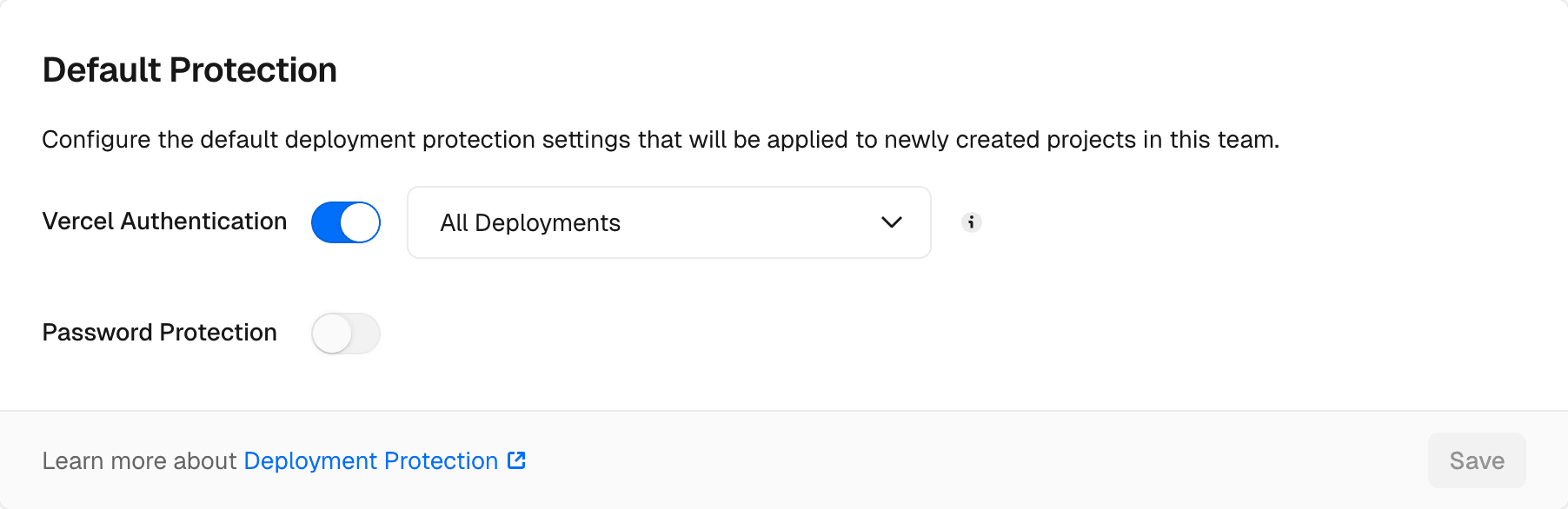
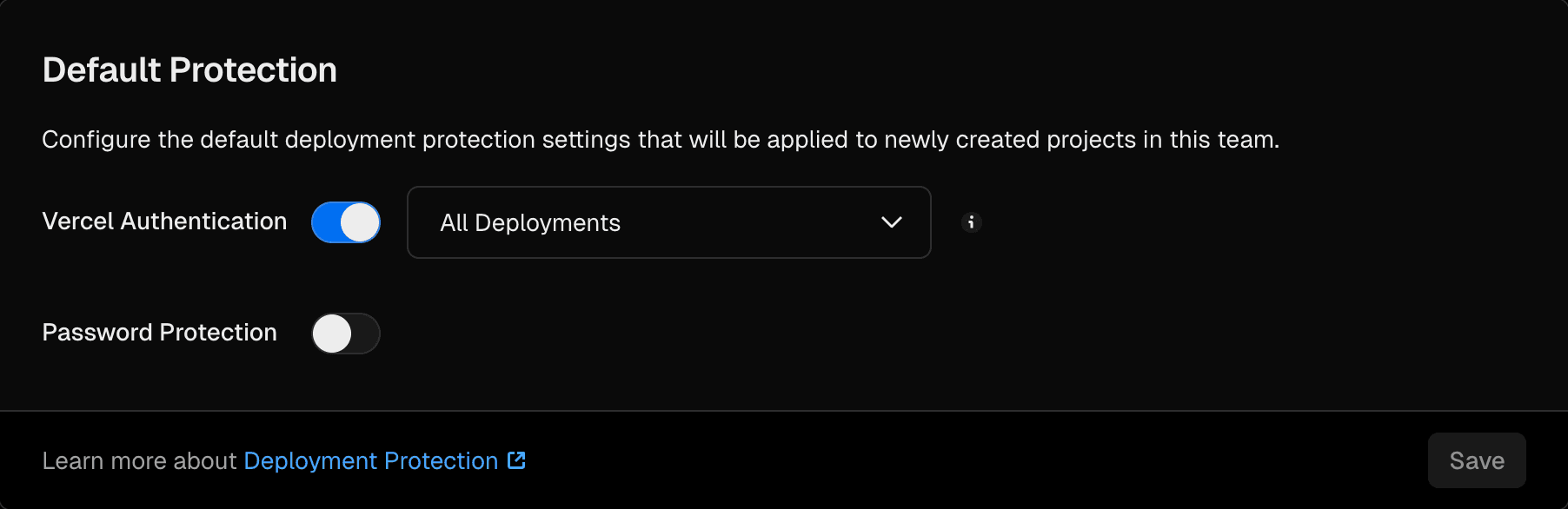
You can set a default Deployment Protection configuration for new projects in your team settings. You can override this default on individual projects as needed.
When setting a team default, choose the protection level (All Deployments, Standard Protection, or None) and the protection method (Vercel Authentication or Password Protection).
Standard Protection is available on all plans
Standard Protection is the recommended option for most projects. It protects all domains except production domains.

You can combine Standard Protection with any of the following methods:
Enabling Standard Protection restricts public access to the production generated deployment URL. This affects VERCEL_URL and VERCEL_BRANCH_URL from System Environment Variables, making them unsuitable for fetch requests.
If you use VERCEL_URL or VERCEL_BRANCH_URL for fetch requests, update your requests to target the same domain the user requested.
The Framework Environment Variable VERCEL_URL is prefixed with the name of
the framework. For example, VERCEL_URL for Next.js is
NEXT_PUBLIC_VERCEL_URL, and VERCEL_URL for Nuxt is NUXT_ENV_VERCEL_URL.
See the Framework Environment
Variables
documentation for more information.
For client-side requests, use relative paths in the fetch call to target the current domain. This automatically includes the user's authentication cookie for protected URLs:
// Before
fetch(`${process.env.VERCEL_URL}/some/path`);
// After
fetch('/some/path');
// Note: For operations requiring fully qualified URLs, such as generating OG images,
// replace '/some/path' with the actual domain (e.g. 'https://yourdomain.com/some/path').For server-side requests, use the origin from the incoming request and manually add request cookies to pass the user's authentication cookie:
const headers = { cookie: <incoming request header cookies> };
fetch('<incoming request origin>/some/path', { headers });Bypassing protection using Protection Bypass for Automation is an option but not required for requests targeting the same domain.
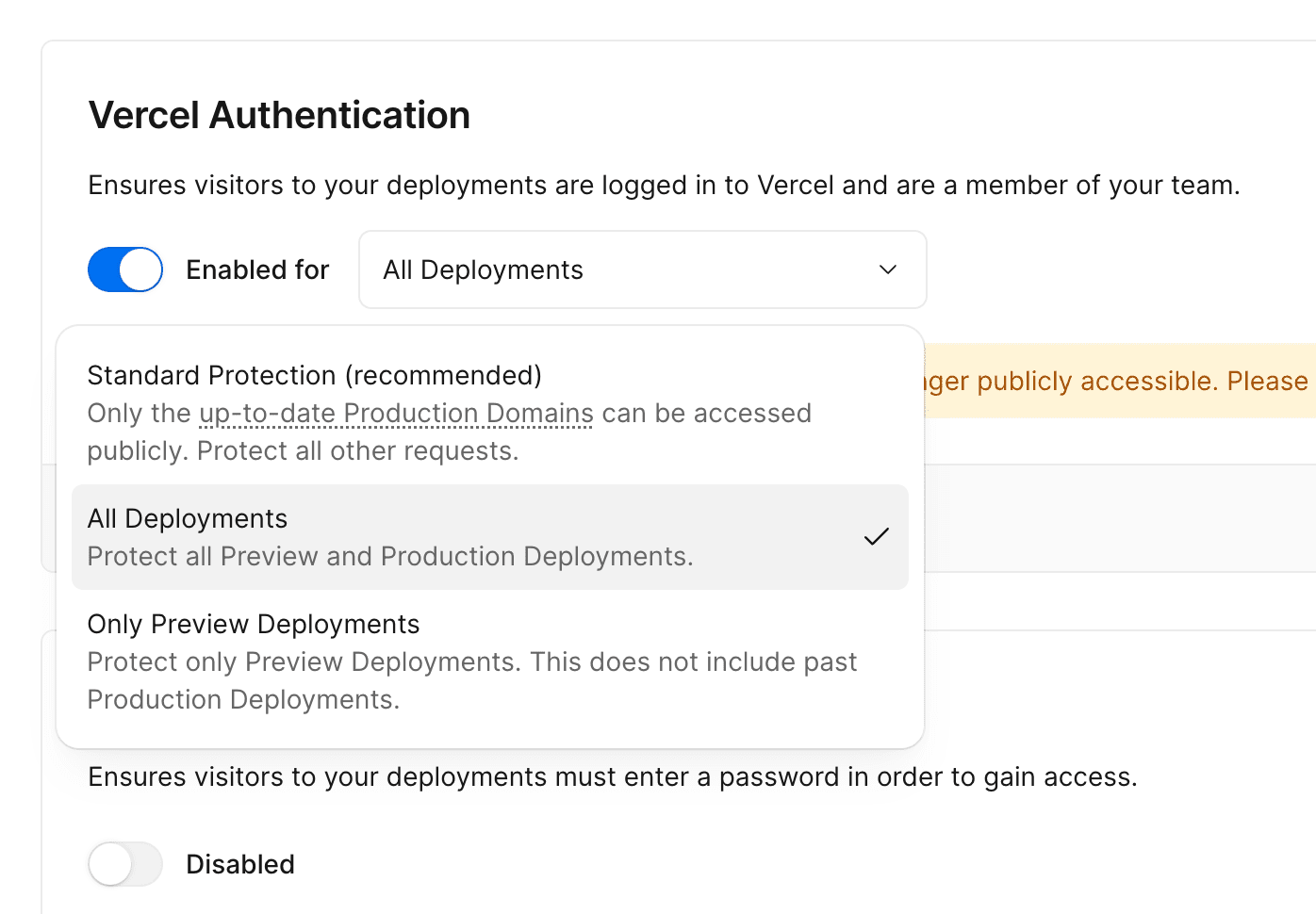
Protecting all deployments is available on Enterprise plans or with the Advanced Deployment Protection add-on for Pro plans
Select All Deployments to secure all deployments, both preview and production, restricting public access entirely.
With this configuration, all URLs are protected, including your production domain example.com and generated URLs like my-project-1234.vercel.app.
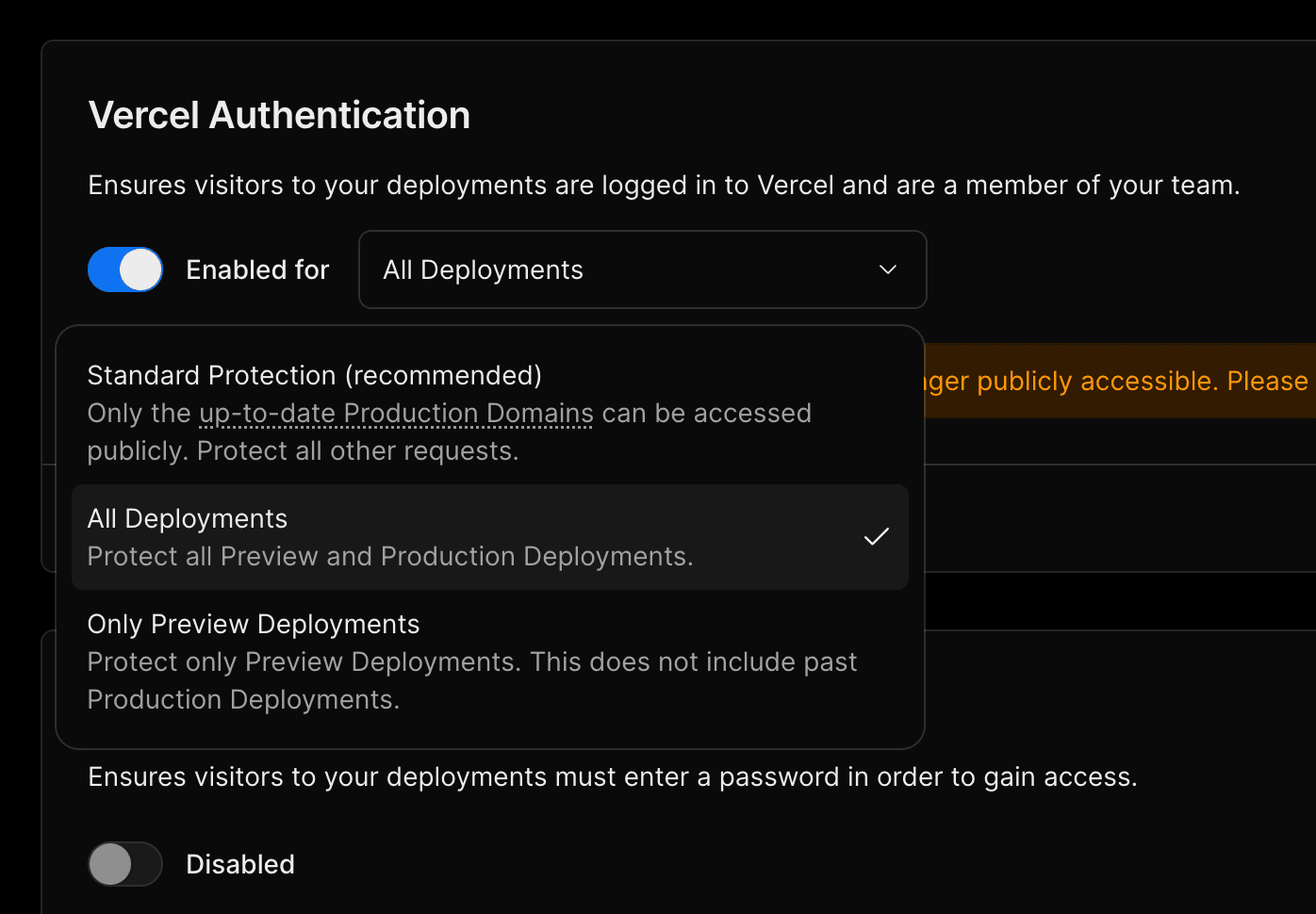
You can combine All Deployments protection with any of the following methods:
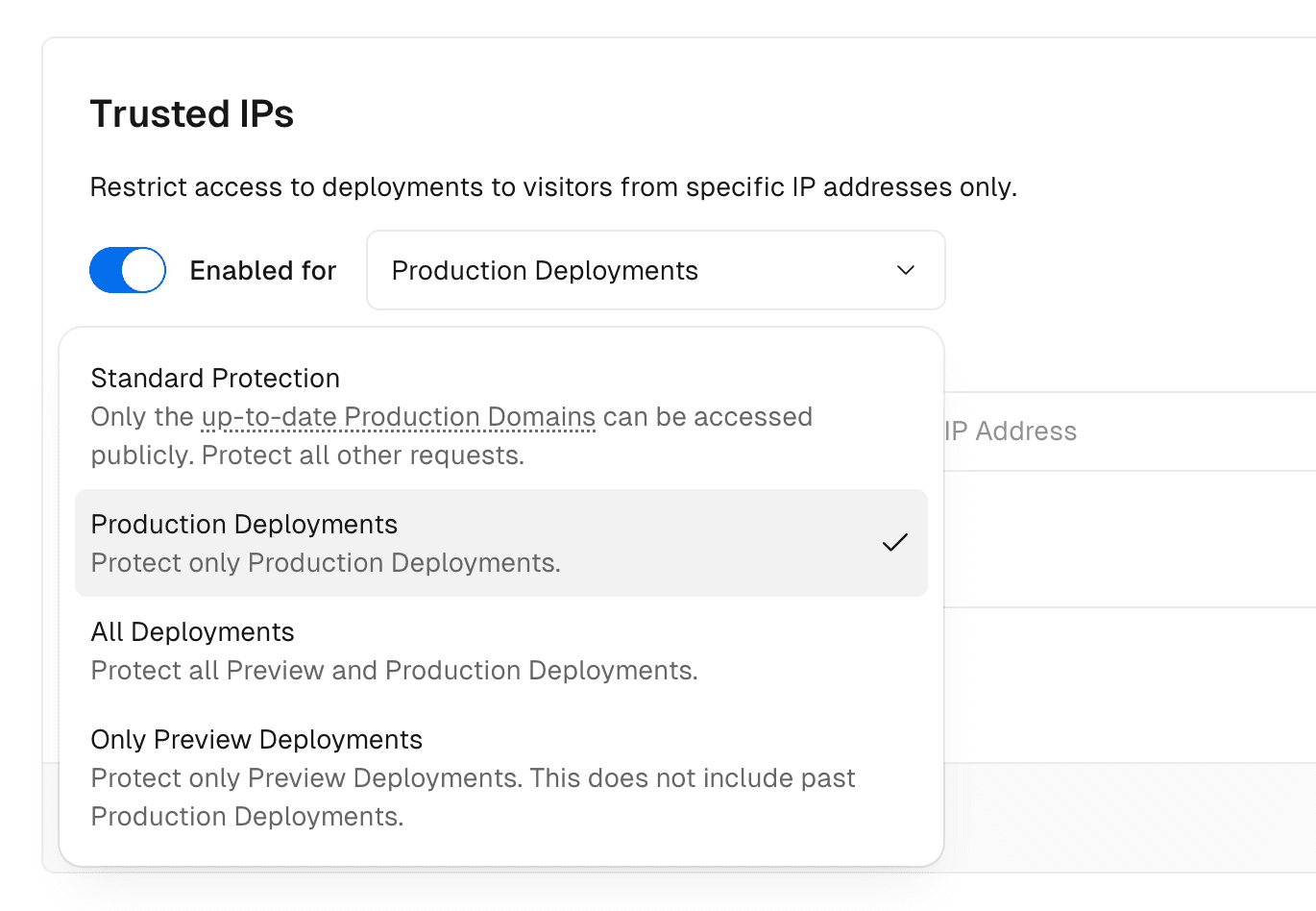
Protecting production deployments is available on Enterprise plans
Use Trusted IPs to restrict access to production deployments to a specific list of IPv4 addresses.
Preview deployment URLs remain publicly accessible. This feature is only available on the Enterprise plan.
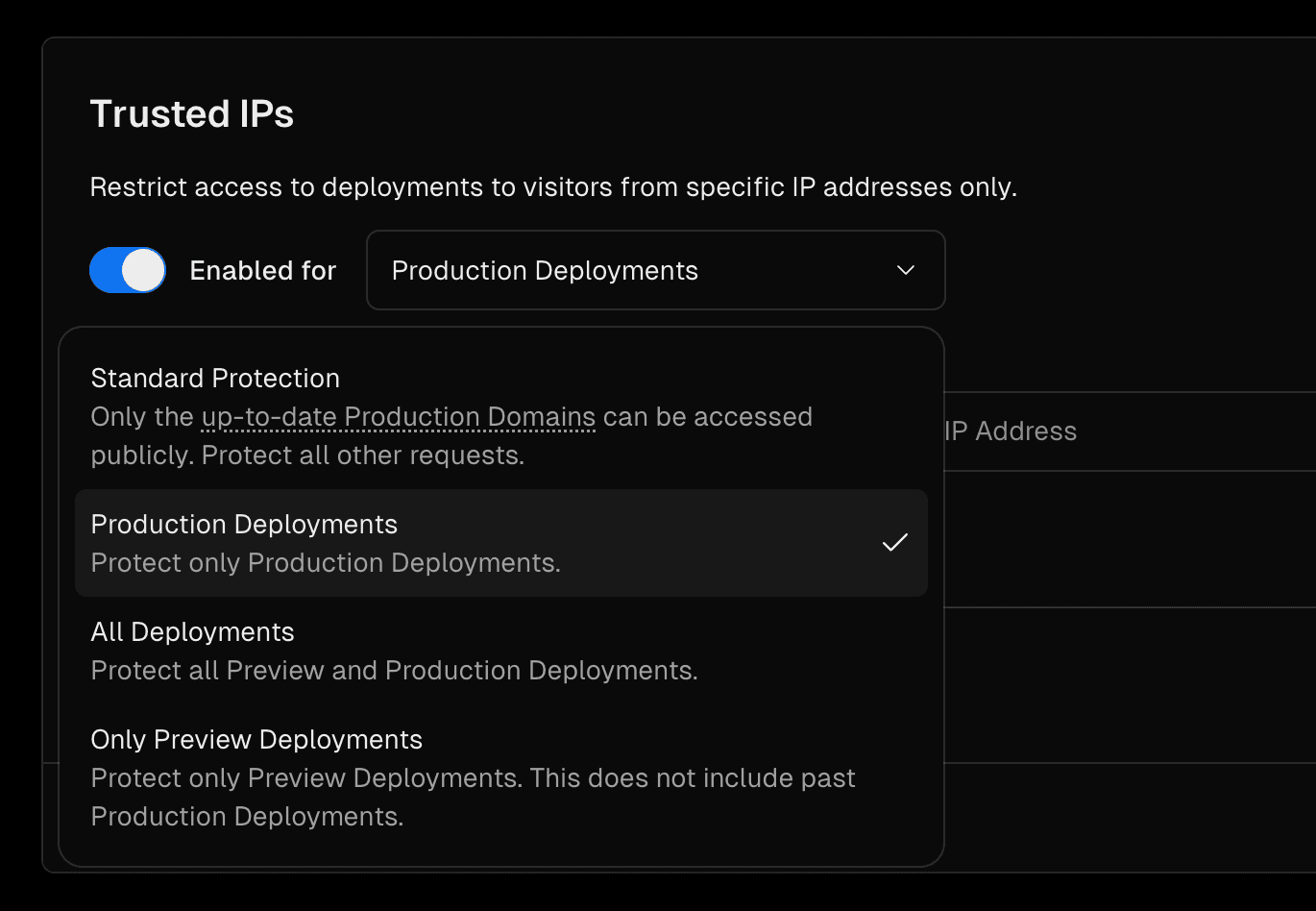
(Legacy) Standard Protection protects all preview URLs and deployment URLs. All up to date production URLs remain unprotected.
Select (Legacy) Only Preview Deployments to protect preview URLs while the production environment remains publicly accessible.
For example, Vercel generates a preview URL such as my-preview-5678.vercel.app, which will be protected. In contrast, all production URLs, including any past or current generated production branch URLs like *-main.vercel.app, remain accessible.
Advanced Deployment Protection features are available to Enterprise customers by default. Pro plan customers can access these features for an additional $150 per month:
To enable Advanced Deployment Protection on a Pro plan:
- Navigate to your project's Deployment Protection settings
- Choose one of the above protection features
- Click Enable and Pay when prompted to upgrade to the Advanced Deployment Protection add-on
When you enable Advanced Deployment Protection, you pay $150 per month for the add-on and gain access to all Advanced Deployment Protection features.
To disable Advanced Deployment Protection:
- Navigate to your team's Billing page
- Click Edit on the feature you want to disable and follow the instructions
You must have used the feature for a minimum of 30 days before you can disable it. Once cancelled, all Advanced Deployment Protection features are disabled.
- Methods to protect deployments: Learn about each protection method in detail
- Methods to bypass deployment protection: Configure exceptions and shareable links
- Vercel plans: Compare plan features and pricing
Was this helpful?

