SAML Single Sign-On
SAML is available on Enterprise and Pro plans
Those with the owner role can access this feature
To manage the members of your team through a third-party identity provider like Okta or Auth0, you can set up the Security Assertion Markup Language (SAML) feature from your team's settings.
Once enabled, all team members will be able to log in or access Preview and Production Deployments using your selected identity provider. Any new users signing up with SAML will automatically be added to your team.
For Enterprise customers, you can also automatically manage team member roles and provisioning by setting up Directory Sync.
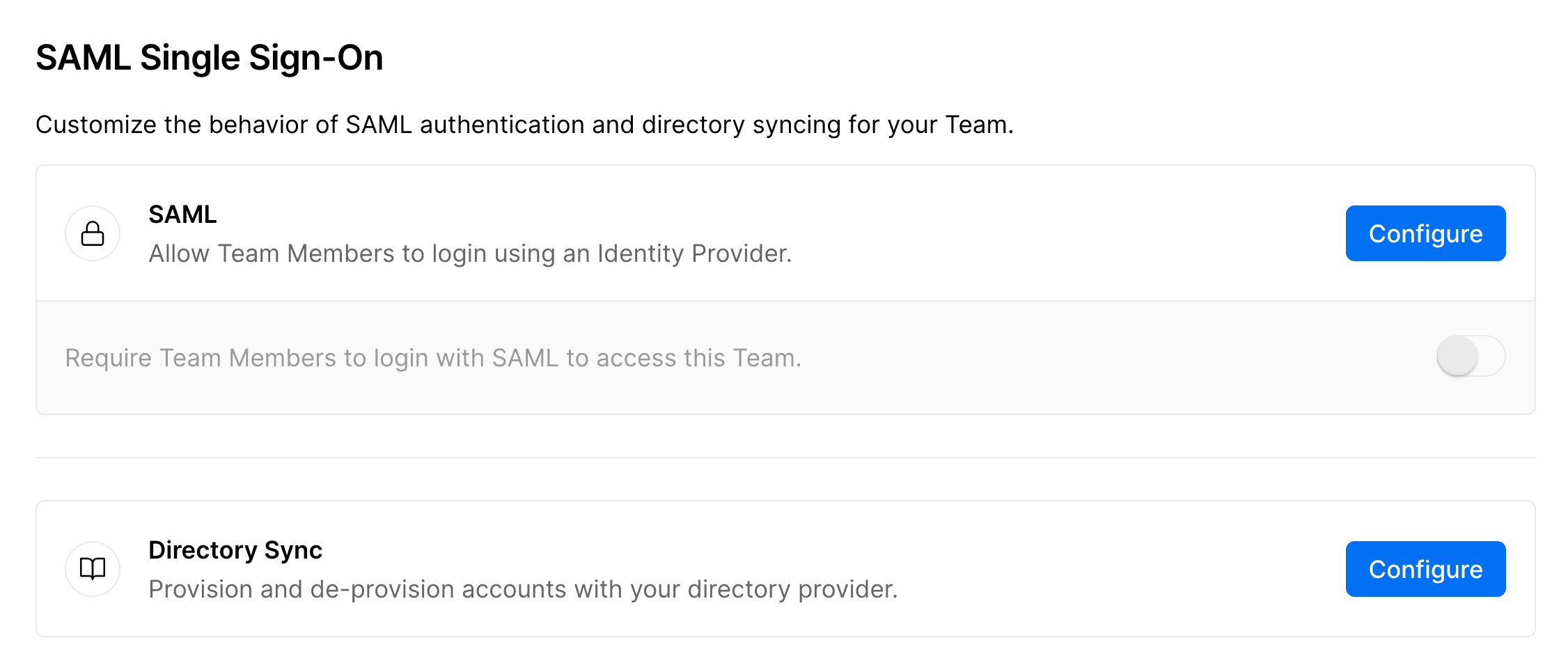
- To configure SAML SSO for your team, you must be an owner of the team
- From your dashboard, ensure your team is selected in the team switcher
- Open Settings in the sidebar and select Security & Privacy
- Navigate to the SAML Single Sign-On section. Click Configure and follow the walkthrough to configure SAML SSO for your team with your identity provider of choice
- As a further step, you may want to enforce SAML SSO for your team
Pro teams will first need to purchase the SAML SSO add-on from their Billing settings before it can be configured.
For additional security, SAML SSO can be enforced for a team so that all team members cannot access any team information unless their current session was authenticated with SAML SSO.
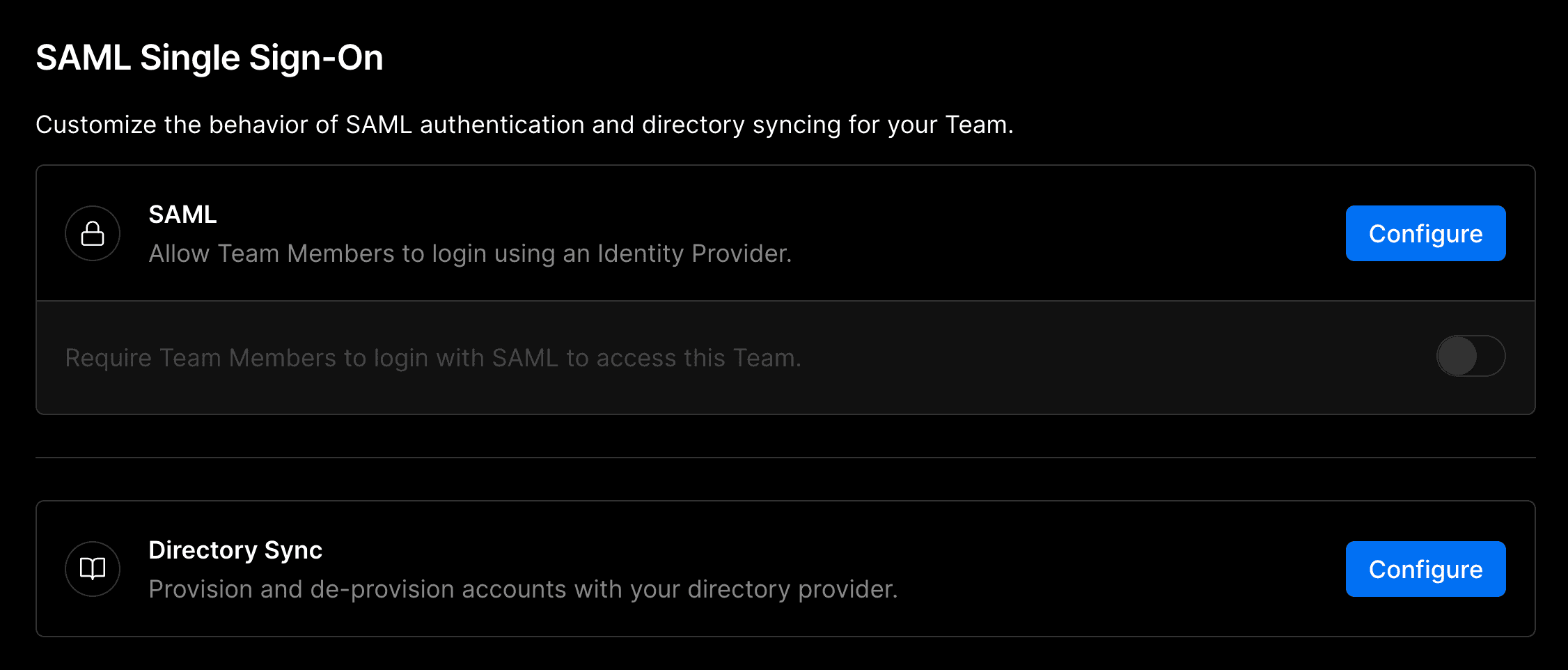
- To enforce SAML SSO for your team, you must be an owner and currently be authenticated with SAML SSO. This ensures that your configuration is working properly before tightening access to your team information
- From your dashboard, open Settings in the sidebar and select Security & Privacy. Then go to the SAML Single Sign-On section
- Toggle the Require Team Members to login with SAML switch to Enabled

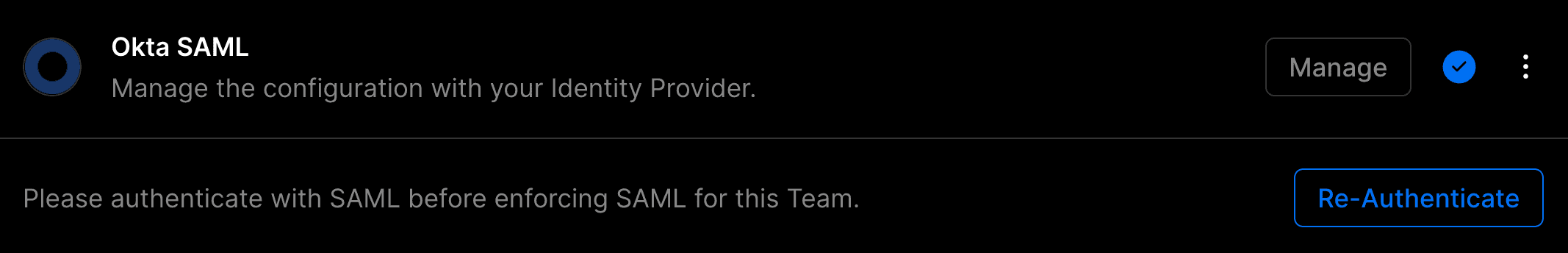
When modifying your SAML configuration, the option for enforcing will automatically be turned off. Please verify your new configuration is working correctly by re-authenticating with SAML SSO before re-enabling the option.
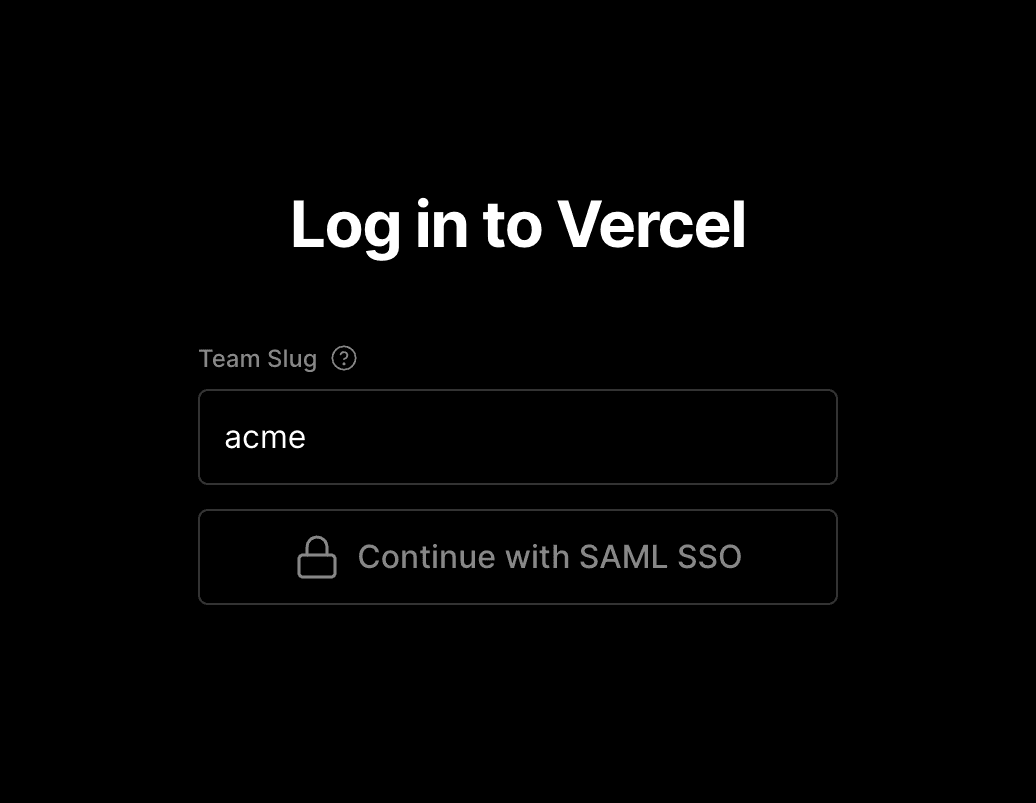
Once you have configured SAML, your team members can use SAML SSO to log in or sign up to Vercel. To login:
- Select the Continue with SAML SSO button on the authentication page, then enter your team's URL.
Your team slug is the identifier in the URLs for your team. For example, the identifier for vercel.com/acme is
acme. - Select Continue with SAML SSO again to be redirected to the third-party authentication provider to finish authenticating. Once completed, you will be logged into Vercel.
SAML SSO sessions last for 24 hours before users must re-authenticate with the third-party SAML provider.
You can choose to share a Vercel login page that only shows the option to log in with SAML SSO. This prevents your team members from logging in with an account that's not managed by your identity provider.
To use this page, you can set the saml query param to your team URL. For example:
https://vercel.com/login?saml=team_id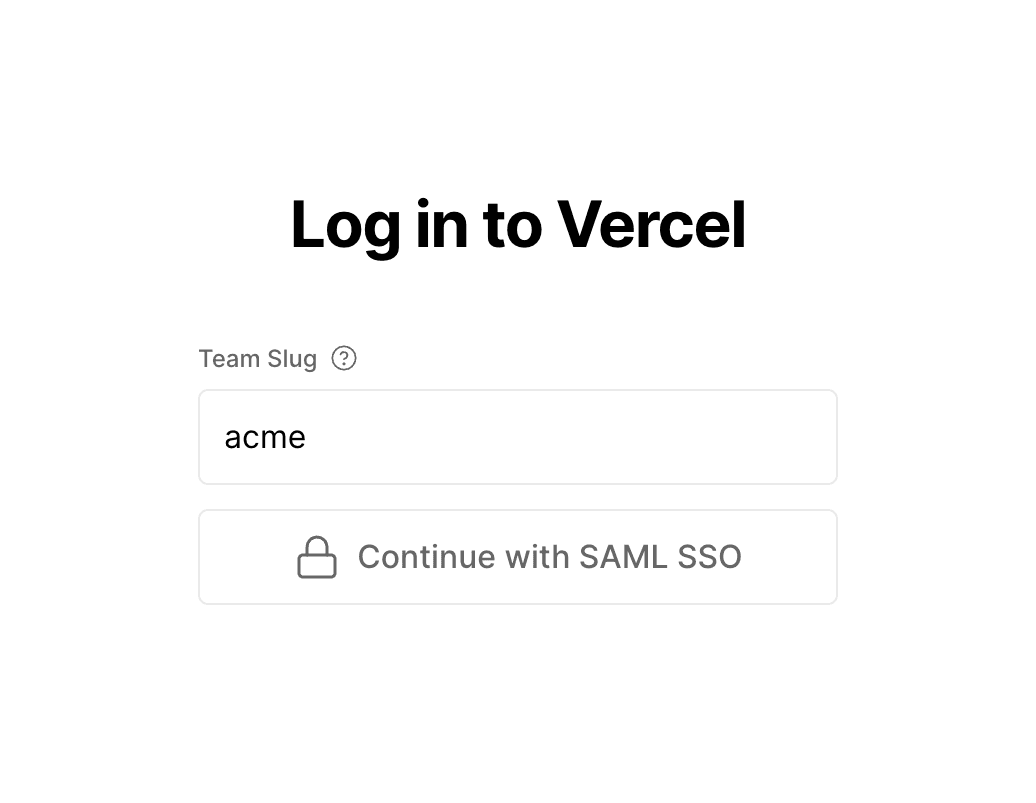
When using SAML SSO, team members can authenticate through your identity provider, but team membership must be managed manually through the Vercel dashboard.
For automatic provisioning and de-provisioning of team members based on your identity provider, consider upgrading to Directory Sync, which is available on Enterprise plans.
Vercel supports the following third-party SAML providers:
Was this helpful?

