Directory Sync
Directory Sync is available on Enterprise plans
Those with the owner role can access this feature
Directory Sync helps teams manage their organization membership from a third-party identity provider like Google Directory or Okta. Directory Sync is only available for Enterprise Teams and can only be configured by Team Owners.
When Directory Sync is configured, changes to your Directory Provider will automatically be synced with your team members. The previously existing permissions/roles will be overwritten by Directory Sync, including current user performing the sync.
Make sure that you still have the right permissions/role after configuring Directory Sync, otherwise you might lock yourself out.
All team members will receive an email detailing the change. For example, if a new user is added to your Okta directory, that user will automatically be invited to join your Vercel Team. If a user is removed, they will automatically be removed from the Vercel Team.
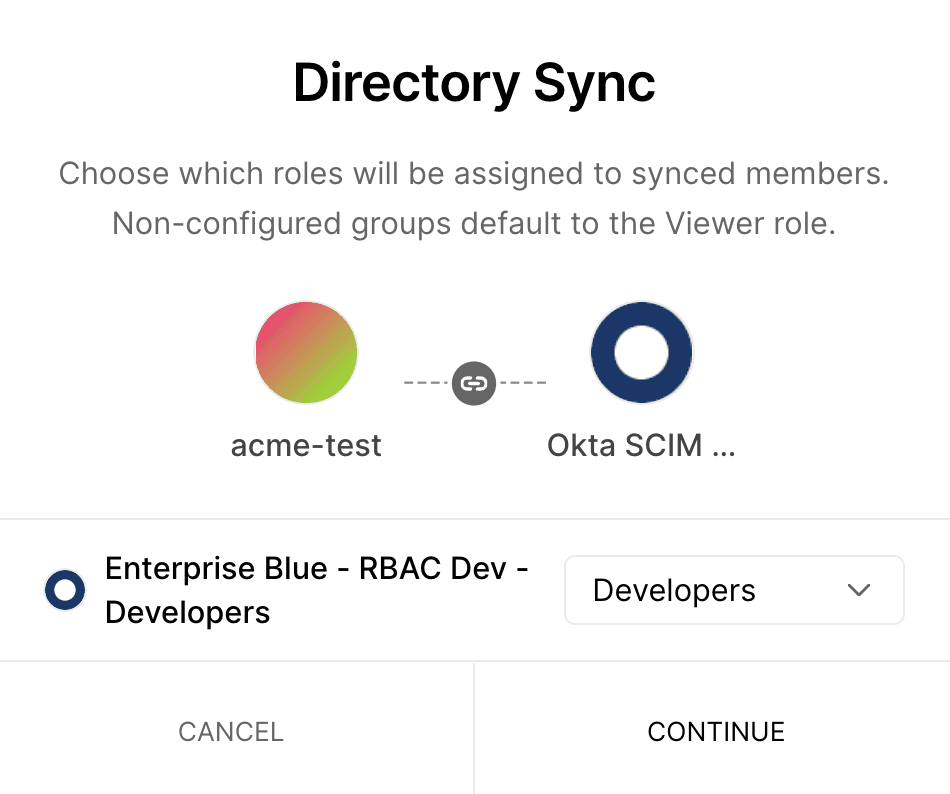
You can configure a mapping between your Directory Provider's groups and a Vercel Team role. For example, your Engineers group on Okta can be configured with the member role on Vercel, and your Admin group can use the owner role.
To configure directory sync for your team:
- Ensure your team is selected in the team switcher
- From your team's dashboard, open Settings in the sidebar, and then Security & Privacy
- Under SAML Single Sign-On, select the Configure button. This opens a dialog to guide you through configuring Directory Sync for your Team with your Directory Provider.
- Once you have completed the configuration walkthrough, configure how Directory Groups should map to Vercel Team roles:
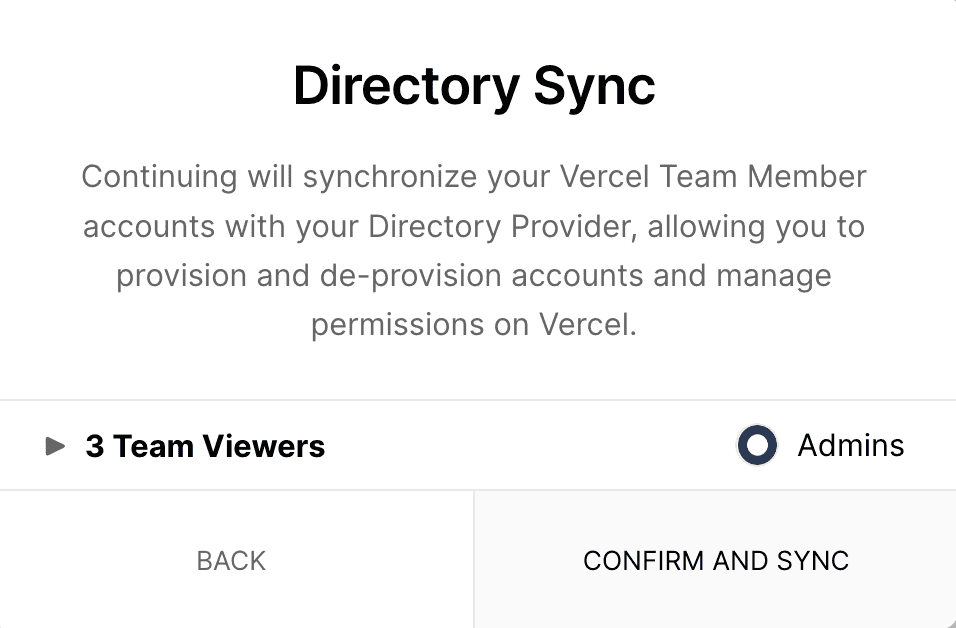
- Finally, an overview of all synced members is shown. Click Confirm and Sync to complete the syncing:
-
Once confirmed, Directory Sync will be successfully configured for your Vercel Team.
SAML Single Sign-On is optionally available on the Enterprise plan, or as a paid add-on for the Pro plan. To enable, Enterprise teams can contact sales, and Pro teams can purchase the add-on from their team's Billing settings.
See SAML Single Sign-On for a list of all the SAML providers that Vercel supports.
To prevent account lockout ensure that at least one person in your team has the owner role, and that they are not removed from the team.
If access is lost due to removal of team owners, use the following group names to automatically allocate the corresponding roles to individuals in that group:
| Group name | Role |
|---|---|
vercel-role-owner | Owner |
vercel-role-member | Member |
vercel-role-developer | Developer |
vercel-role-billing | Billing |
vercel-role-viewer | Viewer Pro or Viewer Enterprise |
vercel-role-contributor | Contributor |
Was this helpful?

