Methods to Protect Deployments
Vercel offers three methods for protecting your deployments. Depending on your use case, you can choose to protect a single environment, or multiple environments. See Understanding Deployment Protection by environment for more information.
You can see an overview of your projects' protections in the following way
- From your dashboard, open Settings in the sidebar and select Deployment Protection
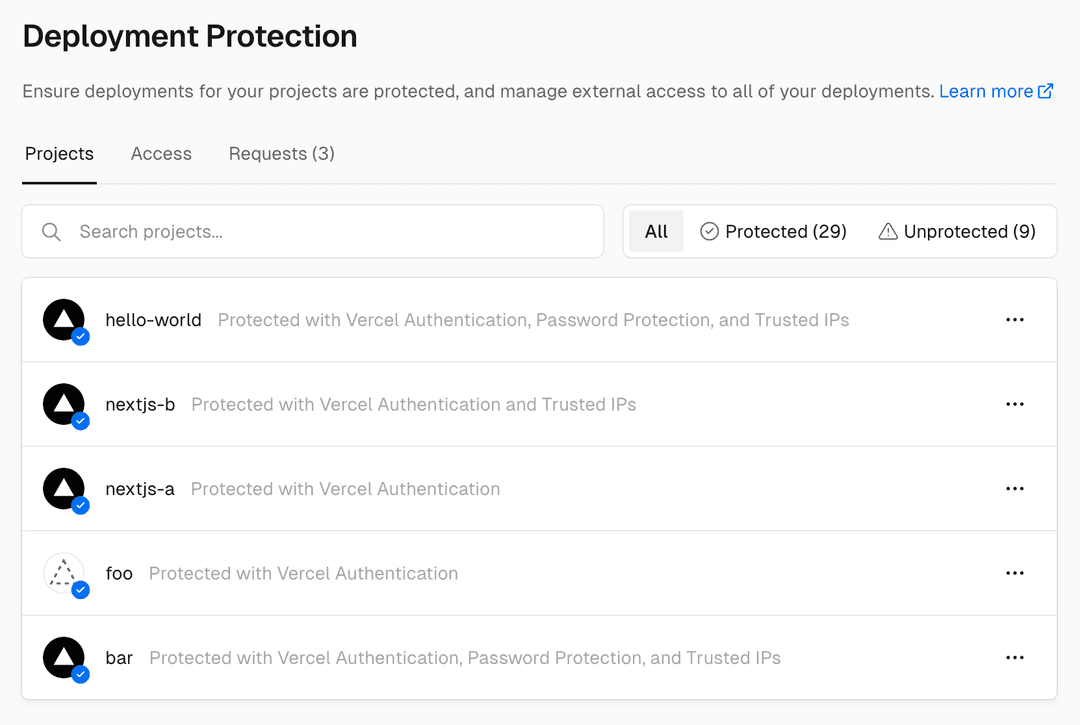
Vercel Authentication is available on all plans
With Vercel Authentication you can restrict access to all deployments (including non-public deployments), meaning only those with a Vercel account on your team, or those you share a Sharable Link with, can access non-public urls, such as my-project-1234-your-name.vercel.app.
When a Vercel user visits your protected deployment, but they do not have permission to access it, they have the option to request access for their Vercel account. This request triggers an email and Vercel notification to the branch authors.
Learn more about Vercel Authentication and how to enable it.
Password Protection is available on Enterprise plans or with the Advanced Deployment Protection add-on for Pro plans
Password Protection on Vercel lets you restrict access to both non-public, and public deployments depending on the type of environment protection you choose.
Learn more about Password Protection and how to enable it.
Trusted IPs are available on Enterprise plans
Trusted IPs restrict deployment access to specified IPv4 addresses and CIDR ranges, returning a 404 for unauthorized IPs. This protection feature is suitable for limiting access through specific paths like VPNs or external proxies.
Learn more about Trusted IPs and how to enable it.
Was this helpful?

